IBMi (AS400) fans only : Encrypting/Decrypting data with RpgFree & SQL embedded
#IBMiSample
Compile and Run this SQLRPGLE. This is an explanation how to encrypt/decrypt data in a DB2 table using RpgFree & SQL embedded.
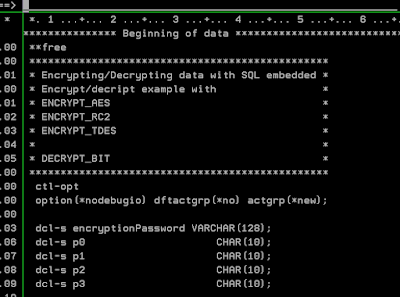
**free
************************************************
* Encrypting/Decrypting data with SQL embedded *
* Encrypt/decript example with *
* ENCRYPT_AES *
* ENCRYPT_RC2 *
* ENCRYPT_TDES *
* *
* DECRYPT_BIT *
************************************************
ctl-opt
option(*nodebugio) dftactgrp(*no) actgrp(*new);
dcl-s encryptionPassword VARCHAR(128);
dcl-s p0 CHAR(10);
dcl-s p1 CHAR(10);
dcl-s p2 CHAR(10);
dcl-s p3 CHAR(10);
// The EXEC SQL is never executed. It is used at compile time.
exec sql Set Option Commit = *none;
// Create File
exec sql
create or replace table TABLE1
(F0TEXT VARCHAR(010),
F1_AES VARCHAR(128) FOR BIT DATA,
F2_RC2 VARCHAR(128) FOR BIT DATA,
F3TDES VARCHAR(128) FOR BIT DATA,
PRIMARY KEY(F0TEXT))
ON REPLACE DELETE ROWS ;
encryptionPassword = 'kljhasdflkjhasdf';
exec sql SET ENCRYPTION PASSWORD = :encryptionPassword ;
// Insert a row
EXEC SQL INSERT INTO TABLE1
VALUES ('aaaa', ENCRYPT_AES( '111111111') ,
ENCRYPT_RC2( '222222222') ,
ENCRYPT_TDES('333333333')) ;
// Insert another row
EXEC SQL INSERT INTO TABLE1
VALUES ('bbbb', ENCRYPT_AES( 'xxxxxxxxx') ,
ENCRYPT_RC2( 'yyyyyyyyy') ,
ENCRYPT_TDES('zzzzzzzzz')) ;
exec sql close C1;
exec sql open C1;
// Read recordset without decription
dow Sqlcode = 0;
exec sql fetch C1 into :p0, :p1, :p2, :p3;
if sqlcode = 0;
dsply p1;
dsply p2;
dsply p3;
endif;
enddo;
exec sql close C1;
exec sql close C2;
exec sql open C2;
// Read recordset with decription
dow Sqlcode = 0;
exec sql fetch C2 into :p0, :p1, :p2, :p3;
if sqlcode = 0;
dsply p1;
dsply p2;
dsply p3;
endif;
enddo;
exec sql close C2;
*inlr = *on;
// Read recordset without decription
exec sql declare C1 cursor for
SELECT F0TEXT,
F1_AES,
F2_RC2,
F3TDES
FROM TABLE1;
exec sql declare C2 cursor for
SELECT F0TEXT,
DECRYPT_BIT(F1_AES),
DECRYPT_BIT(F2_RC2),
DECRYPT_BIT(F3TDES)
FROM TABLE1;
I appreciate all the comments made on this blog.



If just the word AS/400 was replaced with IBM i, I should add this great article to my daily newsletter about IBM i.. www.builtonpower.com/newsletters
ReplyDeleteHallo Tobbe.
DeleteThanks for your comment.
It is true, the right name is IBM i, but AS/400 is the name of the grandfather, you may not know it but in Italy it is traditional to replicate the name of the grandfather in newborns ;-) especially if the grandfather was a great grandfather !
You can explain yourself in your blog why even today a lot of programmers still call it AS/400, due to the efficiency and reliability of the IBM i system that comes from the grandfather.
Hallo Tobbe. I partially accepted your advice, I changed the title of the post with IBMi (AS400) fans only ;-)
DeleteencryptionPassword is set on code as a literal. It's an insecure practice. What is a secure way to manage encryptionPassword?
ReplyDeleteI don't know any other ways. If there is anyone who knows other ways he is asked to show up.
DeleteIn the way I showed in this post, the object must be compiled with the *NOLSTDBG option to not show the source in the debug phase (STRDBG PGMNAME).